Risk Based Vulnerability Management (RBVM) have become widespread across IT environments, while security teams possess limited resources. ...
Remote Desktop Protocol (RDP) is now widely used by businesses to enable remote workforces, but if left ...
Remote Code Execution (RCE) attacks enable hackers to gain access and execute code on systems and devices ...
Red teaming assessments are an indispensable way to assess the strength of an organization’s defenses and identify ...
Red team skills involve simulating real-world cyber attacks and effectively identifying vulnerabilities. It requires highly technical skill ...
An effective Real user monitoring (RUM) solution enables you to rapidly detect errors impacting real users, which ...
Effective ransomware recovery requires a detailed incident response and disaster recovery (DR) plan that evaluates how hackers ...
Here is the 8 Ransomware Protection Strategies – defensive against ransomware requires an all-encompassing effort from all ...
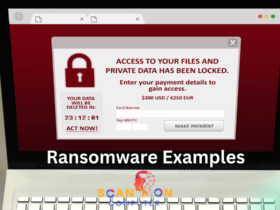
Let’s learn 12 Ransomware Examples with this article. Ransomware attacks can wreak havoc across every sector – ...
Early Ransomware Detection attacks is crucial to protecting organizations from losing data, which requires both automation and ...