Modern endpoint protection tools are cloud-based, making deployment easy and scalable. The best EPP solutions work without or without network connection and upload endpoint telemetry for analysis and threat detection in the cloud.
Signature matching uses an extensive database of known threats to compare files and applications against known threats, and can effectively stop less-than-sophisticated attacks without significantly impacting an application’s performance.
What is Endpoint Protection Software?
Endpoint protection software protects workstations, laptops, servers and other devices connected to company networks from cyber threats by taking measures such as installing anti-malware software and firewalls to keep malicious users away. Furthermore, access control ensures only authorized individuals can gain entry to data stored on those devices.
Enterprise-grade endpoint protection solutions typically incorporate multiple security technologies managed from one centralized console, eliminating the need for technicians to manually configure, manage, update and retire hundreds of endpoints – freeing them up to focus on more valuable and business-critical tasks.
An effective endpoint security solution must provide more than traditional anti-virus and malware protection; it must also include fileless and zero-day attack detection capabilities to address emerging attacks that use polymorphic code or other techniques to bypass signature-based protection tools. Therefore, detection and response capabilities that can detect and neutralize such sophisticated attacks before they cause irreparable harm are vitally important. Ideally, look for EDR solutions with built-in machine learning/analytics.
Benefits of Endpoint Protection Software
Endpoint security solutions protect one of your company’s most prized possessions: its data. Unprotected information can be leveraged by cybercriminals to steal confidential documents, commit corporate espionage and engage in extortion or ransomware attacks that damage a business’ reputation, revenue streams and may put operations at risk of insolvency.
Antivirus and antimalware software remain essential components of an endpoint protection strategy; these applications use signature detection to search file patterns against a database of known threats in order to scan for malware. While they are an integral component of cybersecurity architecture, these tools do not offer complete protection from advanced threats.
Advanced endpoint protection platforms (also referred to as EPP) rely on machine learning and AI technologies to detect advanced threats such as fileless malware, zero-days and ransomware attacks. Furthermore, EPP can utilize continuous raw event recording to gain visibility across your entire network via one central console; threat intelligence collected can then be utilized quickly detect emerging threats more efficiently and speed up their remediation faster – an invaluable way to quickly respond to breaches or incidents that arise in a timely fashion.
Choosing the right endpoint protection software
When choosing an endpoint protection solution, it is key to select a vendor with comprehensive layered security – this should include anti-malware software, advanced threat detection and response (ATDR), as well as various security tools designed to reduce attack surfaces and protect data breaches.
An effective cloud-based solution should be quick to deploy and easy to manage, saving both your IT team time and resources as it expands with your business. Plus, such solutions can easily scale as your company grows!
Make sure that the endpoint protection platform you select uses machine learning and AI to safeguard against modern threats, including fileless malware and zero-day attacks that often avoid traditional antivirus detection by changing their code and altering their behavior.
Finally, seek a solution that integrates DNS security, behavioral detection, automated patch management, ransomware encryption protection, privileged access management, and organizational defense into one seamless approach. One provider that provides this type of defense unified solution is ReasonLabs with their machine learning-powered RAV essentials solution.
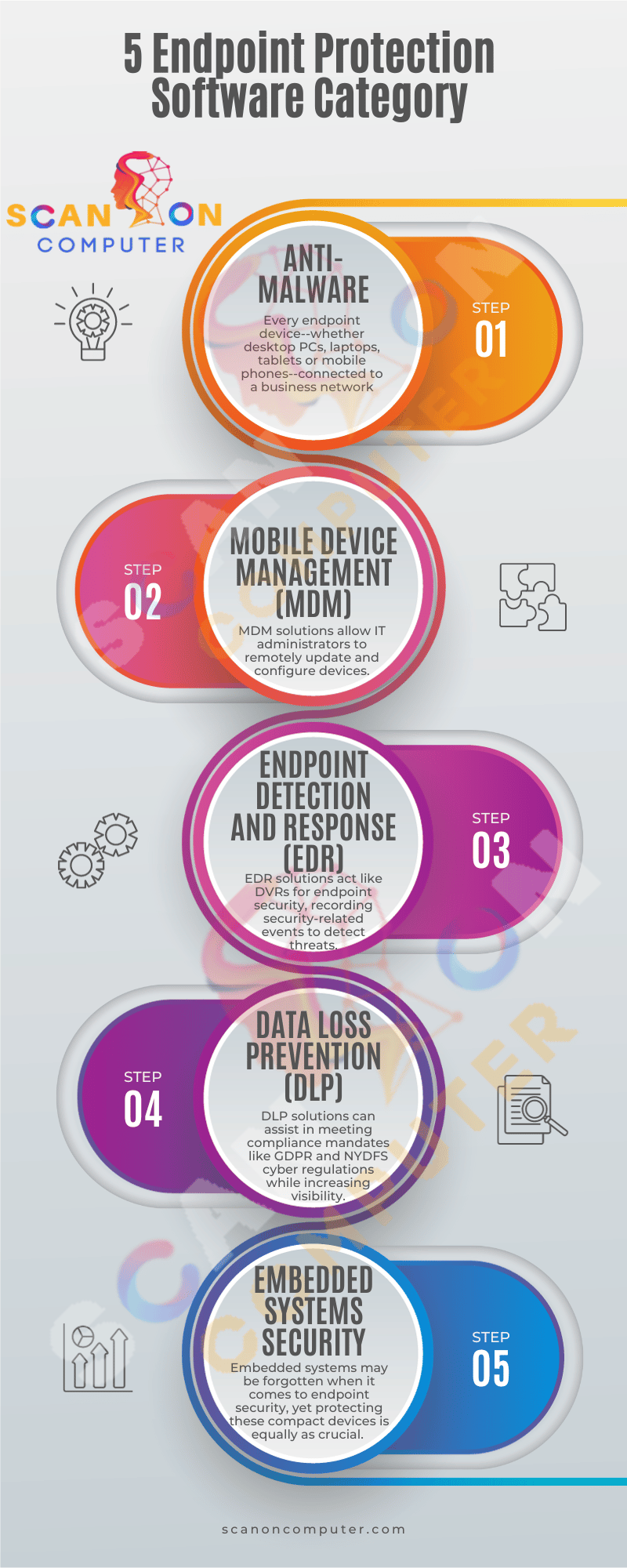
5 Endpoint Protection Software Category
Integral security tools with agents deployed on endpoints that use agents to monitor execution processes and file systems on those endpoints, identify anomalies and address incidents quickly and decisively. Such products often form part of an endpoint protection platform (EPP), which also includes antivirus/antimalware solutions, firewalls and intrusion prevention systems as other security products.
Contrary to antivirus software which utilizes virus signatures for threat detection and removal, advanced technologies rely on machine learning algorithms to analyze file behavior, detect new attack methods, and decrease ransomware attacks that are difficult to identify with traditional antivirus solutions.
Carbon Black EDR provides effective detection and response capabilities while Heimdal stands out with its comprehensive offering that features a central dashboard, threat hunting capabilities, forensics analysis, automated patching capabilities and DNS security protection as well as privilege access management features. Both solutions offer powerful protection for remote workers; however their scanning speeds may lag behind other available solutions, causing delays in identifying incidents that might otherwise have been identified sooner.
Endpoint protection software serves to safeguard business data and systems against cyberattacks at the network edge, designed to detect, analyze, and respond quickly to attacks in progress and stop them before they spread or cause irreparable harm to an enterprise. To be effective, the software must cooperate with other cybersecurity tools and systems in identifying and mitigating threats.
Vulnerability management solutions are an indispensable element of endpoint protection, as they enable enterprises to detect, prioritize and resolve software vulnerabilities in the enterprise environment. Vulnerabilities pose one of the primary risks enterprises must contend with these days due to Bring Your Own Device (BYOD) policies that make securing networks difficult.
Traditional antivirus is no longer enough to keep malware away from an enterprise; hackers have become adept at changing malware files so they no longer match what the anti-virus software recognizes. To combat such attacks, advanced security solutions offer various prevention and response features such as next-generation anti-malware technology with behavior intelligence capabilities; sandboxing; deception technologies; as well as continuous raw event recording for post-event analysis and forensics through one console for faster incident response.
1. Anti-malware
Every endpoint device–whether desktop PCs, laptops, tablets or mobile phones–connected to a business network represents an entryway for cyber criminals. Employees working from both office locations or remotely could inadvertently open corrupted content or click on malicious links in phishing emails that will infect their devices with malware used to steal sensitive data or cause other forms of damage.
An EPP solution should offer advanced antimalware/AV detection that uses signatures to inspect files for characteristics associated with known threats and behavioral analysis to expand protection and detect malware that evades signature-based detection. Furthermore, least privilege management capabilities (also called Privilege Elevation and Delegation) reduce the attack surface by only permitting access when required, helping ward off lateral attacks, ransomware attacks and zero day exploits from entering systems.
2. Mobile device management MDM
As work-from-home trends expand, Mobile Device Management (MDM) solutions enable organizations to support BYOD policies without jeopardizing employee privacy. These solutions serve to separate personal from work data on devices belonging to employees; thus preventing private information from entering company networks via employees’ devices. In addition, MDM solutions feature compliance regulations like GDPR, HIPAA and PCI-DSS with features for meeting regulatory standards like these.
MDM solutions allow IT administrators to remotely update and configure devices over-the-air without interrupting user experience, and contain device diagnostics capabilities for quick detection and resolution of issues.
There are various powerful MDM solutions to fit every business need, but choosing the most appropriate one depends on the resources available and security requirements of your solution. When selecting an MDM platform that offers both software as a service (SaaS) models and on-premises platforms, SaaS solutions may provide faster implementation and lower operational costs compared to on-premises platforms.
3. Endpoint detection and response EDR
EDR solutions act like DVRs for endpoint security, recording security-related events to detect threats that evade prevention tools. By analyzing data traffic on the endpoint and searching for patterns indicative of cyber threats or indicators of compromise (IOCs), EDR provides tools for investigation and responding to these potential cyber attacks.
Advanced EDR tools use advanced analytics to distinguish real threats from false positives, reducing alert fatigue. They may also integrate with SIEM solutions for additional context on which to base prioritizing and investigating threats.
As businesses increasingly shift toward distributed work environments, businesses require a centralized method for monitoring and managing endpoints to prevent disruption and limit any impact from cyberattacks on their bottom line. EDR solutions provide faster incident response times; reduce dwell time of attackers; help businesses recover after cyber attacks; retrieve affected files faster.
4. Data loss prevention DLP
With data breaches becoming more frequent and costly, businesses require stringent security measures. DLP tools provide businesses with additional protections by monitoring files, emails and other types of communication for sensitive information to prevent it being shared externally. They can also log incidents for auditing purposes or notify employees if they accidentally share confidential data via email, web chat or other platforms.
DLP solutions can assist in meeting compliance mandates like GDPR and NYDFS cyber regulations while increasing visibility into your internal systems. Furthermore, it can adapt with changing global regulatory requirements so your organization is always ready for whatever challenge may come next.
DLP solutions can be deployed either at the network edge or endpoints to secure both data in motion and at rest. DLP systems can monitor a large variety of connected devices – including remote work and BYOD systems – connected to your business as well as their security posture, only permitting compliant devices into your enterprise and thus reducing attack surface.
5. Embedded systems security
Embedded systems may be forgotten when it comes to endpoint security, yet protecting these compact devices is equally as crucial. Their small size, limited computing power and specific functions pose unique cybersecurity challenges which could have detrimental ramifications on their security.
Poor authentication of embedded systems is one of the primary obstacles to its effective operation, making it easy for intruders to gain unauthorized entry. Software should reject all external communication until it has been approved as appropriate and trusted – this ensures an attacker cannot exploit vulnerabilities on just one device to compromise an entire system.
One major challenge relates to an inadequate partitioning of hardware components. Software should only have access to those parts necessary for its function, limiting malicious code attacks on vulnerable areas of the system while increasing overall system security.
As part of an embedded system’s ongoing maintenance plan, it’s also crucial that its firmware can be regularly updated with digitally signed updates. Furthermore, they should connect to an infrastructure which offers regular security patches, helping avoid many of the vulnerabilities experienced by other systems.
Final Thoughts
Selecting the appropriate endpoint protection software ensures that all devices and systems owned by your business are accounted for, which helps your team focus more time on activities which will advance business growth.
An appropriate tool may also save your company money in the long run. Cyberattacks aren’t cheap, and dealing with one could even become more costly if an incident damages its reputation.
Standard EPP solutions should include anti-malware and anti-ransomware protection, firewall security, central security logging and reporting capabilities as well as more sophisticated features such as insider threat detection, content web filtering, ZTNA VPN functionality as well as vulnerability management – some may even allow systems to revert back to pre-infected states!
Nearly every organization will experience some form of cyberattack at some point, yet with proper solutions in place most cyberattacks will be prevented, ensuring your data stays protected. Remember: the best security tools are those that are in place before any hackers have done any damage; these are proven ways of stopping cyberattacks before they have any lasting repercussions for your business – that is why it pays to thoroughly research endpoint protection software options available today.














Leave a Reply
View Comments