Wazuh is a free and open-source monitoring solution equipped with sophisticated XDR and SIEM capabilities, featuring multi-platform agents capable of detecting local security issues on endpoints like laptops, desktops, servers, containers and virtual machines.
System and application configuration settings are continually monitored, to ensure compliance with security policies. Furthermore, periodic scans are run in order to identify applications known to be vulnerable or poorly configured.
Integrity Monitoring
Wazuh’s Integrity Monitoring feature offers a set of tools to strengthen security controls and fine-tune your framework to address various threat concerns, from making sure systems remain secure over time to monitoring changes to files and directories for suspicious activity – this helps prevent data loss due to malware attacks and helps meet regulatory compliance standards like PCI DSS or NIST 800-53.
This solution detects changes to files and their attributes such as checksums, ownership, permissions and more. The FIM module compares recent versions against their baseline versions to generate alerts when there are discrepancies; additionally it can identify users who modified a file, so you can take immediate action against anyone altering one immediately. With cross-platform support it also lets you monitor any file changes across your IT infrastructure regardless of endpoint count.
FIM tracks changes to files using malware signatures and CDB lists (constant database of known indicators of compromise). By matching field values from FIM alerts with those found in CDB lists, FIM detects malware more quickly, thus shortening Mean Time To Respond (MTTR) times and blocking threats in real-time.
Wazuh can monitor and analyze operating system and application logs to detect misconfigurations or indicators of compromise using signature-based analysis or custom rules that align with your policies, standards, or hardening guides.
The platform also performs periodic scans on your systems and applications to assess whether any known vulnerabilities or insecure configurations are impacting them. It detects hidden files, disguised processes and unregistered network listeners – then recommends any necessary remediation measures for remediation.
Wazuh’s integration with ServicePilot allows it to read syslogs in real time and integrate them with its web interface in real-time, providing real-time threat detection, Machine Learning analytics, custom maps, dashboards, automated PDF reports and more – making managing security solutions much simpler than before. Wazuh provides an easily manageable unified view of security events for simplified management.
Incident Response
Wazuh is a free and open source security monitoring solution, featuring prevention, detection and response capabilities. Comprised of an agent, server, and dashboard for easy use in monitoring data centers, public clouds and on-premise environments alike – Wazuh provides a scalable yet flexible approach that adapts easily to different threat vectors or environments while helping organizations meet compliance standards while strengthening and fine-tuning existing security controls.
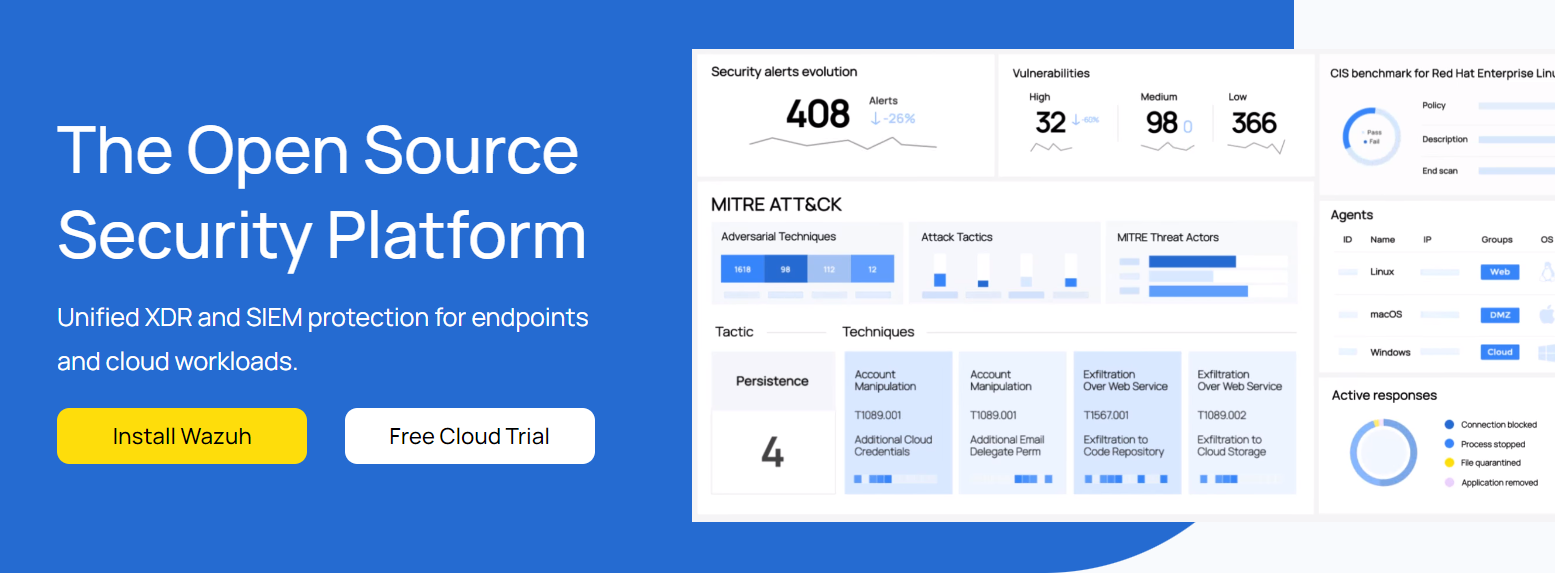
Security Alert Analysis
Wazuh agents monitor operating systems, applications and cloud infrastructures to capture security events before sending them directly to its server for analysis based on configured rules using threat intelligence to search for indicators of compromise as part of its extended detection and response (XDR) capability. An indexer efficiently stores generated data so queries and retrieval can occur swiftly.
Wazuh agents not only collect log data but can also detect anomalous behavior such as hidden files or processes that run without authorization. Wazuh utilizes signature-based intrusion detection with regular expression engine to examine collected logs for signs of malicious activity or other vulnerabilities. Furthermore, Wazuh features file integrity monitoring by monitoring changes to content permissions ownership attributes of files as well as who made those changes and by tracking down who initiated these modifications.
Proactive Vulnerability Detection
Wazuh performs periodic scans of installed applications and operating systems to identify any unpatched or misconfigured vulnerabilities, helping protect you against falling prey to malware and maintaining strong defenses by staying ahead of any potential attack surface.
Wazuh’s incident response feature allows you to automate actions in response to detected incidents, such as deleting malicious files, blocking suspicious network connections, quarantining compromised endpoints and disabling compromised user accounts. Wazuh helps reduce Mean Time to Respond (MTTR) by streamlining and improving your response process and mitigating threats effectively; you can set stateful active responses that revert after a specified period.
Regulatory Compliance
Wazuh provides compliance support through monitoring, reporting and automation. It detects attacks, system anomalies, user actions that violate security policies and misconfigurations as well as monitors and enforces hardening guidelines and security misconfigurations. Wazuh monitors attacks against systems as well as user actions taken against security settings as well as attacks by attackers against them.
Wazuh provides support for PCI DSS, HIPAA, NIST 800-53, TSC SOC2, and GDPR frameworks and standards. The platform’s default ruleset maps alerts to compliance tags in order to help identify compliance gaps and risks; its configuration block capability also enables you to define responses – from blocking hosts from identified threat sources to running remote commands for live forensics and incident response purposes – when threats or vulnerabilities are detected.
Wazuh FIM module helps detect unauthorised modifications to important files and directories by monitoring their contents, storing the cryptographic checksum and attributes as baseline files for comparison, then compares new or modified files against this baseline; if they differ, an alert will be raised immediately. Wazuh can be integrated with vulnerability databases or scanners in order to quickly identify vulnerable systems or applications missing patch updates.
Once an alert is generated, Wazuh server handles its response by communicating with agents to execute it. In addition, logs and information from agents are collected and analyzed so you can receive contextualized reports which provide useful data that allows for further investigations or uncovering potential causes of incidents.
Wazuh provides security operations centers (SOC) teams with centralized dashboards and alert management features that help prioritize and investigate security events quickly, so they can take quick actions to contain or mitigate security incidents while keeping business operational. Furthermore, Wazuh offers guidance and recommendations on how to respond to certain incidents, shortening resolution time.
Wazuh goes beyond its core capabilities to deliver advanced analytics with MISP integration to gain greater insight into threats and attack vectors within your infrastructure, improving threat detection. Furthermore, its XDR feature integrates with external solutions like PagerDuty and TheHive for incident response purposes while cloud security features include monitoring cloud environments at an instance level as well as container protection capabilities.
Threat Detection
Wazuh provides an open source XDR/SIEM solution designed to enable proactive threat detection, automated incident response and system security posture optimization. It consists of an endpoint security agent and management server; with the former running on endpoints you want monitored and providing prevention, detection and response capabilities while the latter collects and analyzes agent data using decoders/rules that detect patterns/icon compromise/other anomalies such as Wazuh uses the MITRE ATT&CK threat database cross-referencing any identified threats providing alerts that can trigger responses quickly allowing proactive response options as quickly as possible.
Wazuh can detect numerous common security threats, including hidden files and processes as well as inconsistencies between system call responses and file integrity changes. Furthermore, its platform can integrate with vulnerability scanners and databases to identify known vulnerabilities within installed applications or operating systems.
Wazuh provides visibility into the security configuration of cloud infrastructure, enabling you to monitor images, volumes, network settings and running containers at an instance level. Integration with Shuffle SOAR enables users to automate remediation workflows triggered by alerts generated by Wazuh.
Wazuh can enhance its intrusion detection capabilities by integrating with malware analysis tools such as Malwarebytes and Yara, providing accurate lists of threats requiring immediate attention in your network. This enables Wazuh to recognize any potentially malicious activities on the network quickly and provide alerts accordingly.
Wazuh can detect more advanced threats by detecting rootkits and other types of hidden software, while when combined with Cuckoo as a malware sandbox it allows for identification and protection against download and execution of such applications.
Integrate Wazuh with Seek for Linux binary analysis tooling to detect potentially malicious or suspicious binaries on your systems, using Wazuh manager to collect Seek’s reports and alerts and generate notifications when Seek finds unusual patterns or indicators of compromise, providing valuable insight into potential attackers who have bypassed other security tools. This method may prove especially beneficial in tracking down attackers that have managed to bypass other protection solutions.
Wazuh Vs OpenEDR
Wazuh is a free open source platform offering threat detection, incident response and compliance monitoring services and it is more or less similar to OpenEDR and there are more Free EDR available online these days. The tool synchronizes data from endpoints, servers, firewalls, email gateways and cloud workload security sources and integrates security analytics and visualization tools for an overview of security posture.
Wazuh intrusion detection capabilities enable it to monitor for and alert on suspicious files, processes and network listeners – such as hidden ones – such as hidden files, processes that run without being noticed, unregistered network listeners and inconsistencies between system call responses and system call responses. Furthermore, Wazuh’s agent/server component uses a regular expression engine to search log data for indicators of compromise.
Additionally, the platform facilitates system and application configuration assessment. Through this function, agents monitor their systems and applications to ensure compliance with security policies such as CIS (System Hardening). Periodic scans detect software known to be vulnerable or improperly configured while security policy checks can be tailored specifically to an organization’s requirements.
Wazuh also supports file integrity monitoring to detect any changes made to system files that could potentially compromise its integrity. The FIM module on the platform stores checksums and attributes of files or Windows registry keys into a local database before continuously monitoring for any differences, alerting when changes are detected.
Wazuh offers active responses that help address threats, such as blocking access from threat sources when certain criteria are met. Furthermore, this platform integrates with VirusTotal for scanning and analysis of files suspected to contain malware.













Leave a Reply
View Comments